Subject D : Secure photonic network architecture
157D-T01Architecture to install QKD systems into existing mission-critical-secure networks
NEC Corporation (Shione Asami)
Hokkaido University
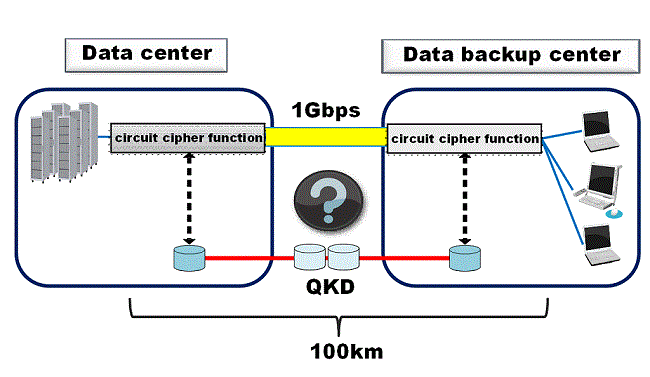
A higher priority in applications of our high-speed QKD systems is the one for state secret communications. Secure crypto-keys for one-time pad are conventionally delivered by trusted couriers. This system can be replaced with an automatic key delivery by a QKD network. Another important one is an application to secure data-backup communications. After the Great East Japan Earthquake, the importance of business continuity planning and constructing data backup networks for it has been widely recognized. QKD should be used to tightly protect transmission of confidential data between data centers. and to make a mission-critical-secure communications system for the above purposes. We also develop an architecture of secure photonic network to provide multiuser secure services for medical networks, smart community networks, and so on.
We develop secure photonic network architecture by the following four subthemes:
- Subtheme 1: Base-line model
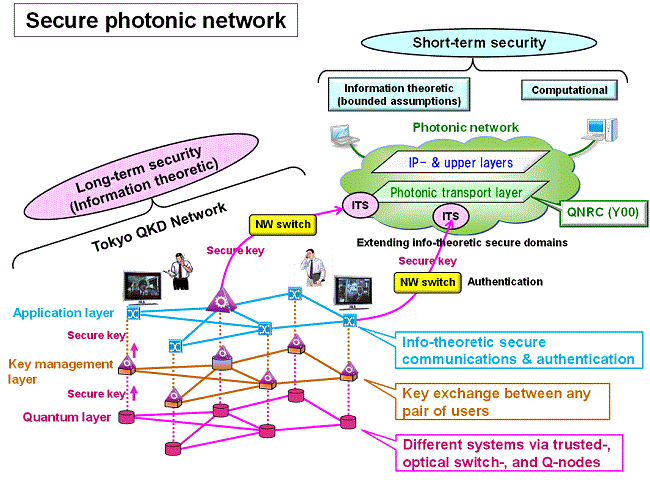
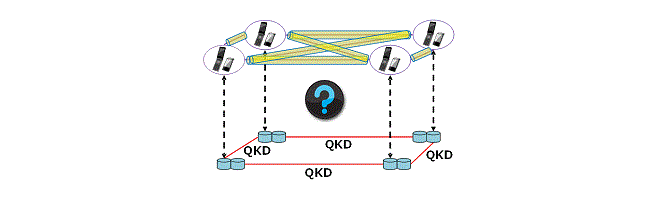
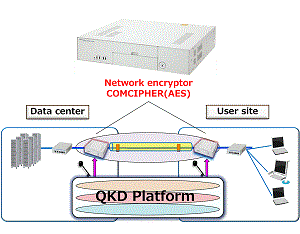
We derive baseline models for point-to-point link and point-to-multipoint network, which define the elements and specifications of the network, taking into account target applications. Figure 1 depicts a rough image of a baseline model.
- Subtheme 2: Application of related peripheral technologies for management
A secure photonic network must provide functions, such as authentication, key distribution and synchronization between several nodes, management of valid key. We develop an architecture for QKD network by integrating and customizing various technologies developed in modern cryptographic networks. The result will be integrated with quantum technology developed in subtheme 3.
- Subtheme 3: Quantum cryptography technology for secure network management
We explore quantum cryptographic technology useful to construct secure network. We collaborate with Subjects 157A, 157B, and 157C, to modify the QKD system suitable to be adopted in the network. Finally, subtheme 2 and subtheme 3 develop optimized architecture in terms of security and network resource.
- Subtheme 4: Construction of test environment / Operation verification
We evaluate technologies developed by subtheme 2 and subtheme 3 in practice. We develop a test environment according to the base-line model defined in subtheme 1.
We study methods to combine the QKD technologies from Subjects 157A, 157B and 157C.
We construct a test service network according to the specification of the systems developed by Subjects 157A, 157B and 157C. It includes a sensor network system to monitor environmental conditions of optical fibers, interfaces, and status of the key management server and agents. Through test runs, data for quality guarantee of our secure photonic network will be extracted.
Final results for Team 157D-T01
| Task title | Outcome | Date | Note |
|---|---|---|---|
| 1: Research for baseline model (Fig. 2-1,2-2,3,4) |
We defined communication model of 1 to 1 and communication model of 1 vs. many as a baseline model. | Oct. 2013 | |
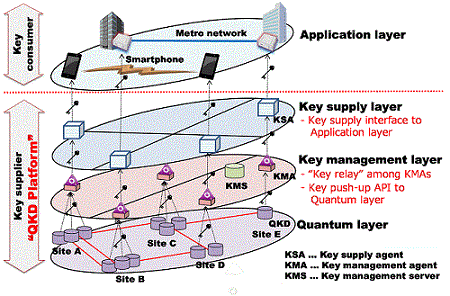
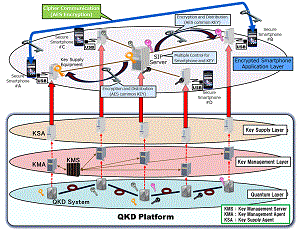
| We defined a three-layered structure (QKD layer, key management layer and key supply layer) and I/Fs between each layer for key distribution. | Mar. 2016 | It became possible to supply secure-key from QKD equipment to various applications. Administration of key supply and applications were separated. QKD platform: key supplier Applications: key user |
|
| We confirmed that an optical fiber tapping and an obstacle can be detected by statistics informations of QKD (QBER, key generation rate) monitoring. | Mar. 2016 | ||
| 2: Application of related technologies for management (Fig. 5-1,5-2) |
We have developed applications to prove the baseline model (Layer 2 network encryptors and Encrypted smartphone). | Mar. 2016 | |
| We introduced authentication systems for key synchronization and identification in the QKD platform (Wegman-Carter authentication). | Mar. 2016 | ||
| We implemented general-purpose physical I/F for key supply. | Mar. 2016 | ||
| 3: Quantum technology for secure network management (Fig. 6) |
We have developed method and technique to characterize working QKD machines. | Mar. 2016 | |
| We proposed a key relay protocol using less-trusted nodes, with the help of classical secret sharing. | Mar. 2015 | ||
| We have developed low-cost photon detectors for monitoring QKD equipment. | Mar. 2015 | ||
| We proposed entanglement recovering from bound entanglement by super-activation. | Mar. 2014 | ||
| 4: Construction of test environment/ Operation verification (Fig. 4,7,8,9,10) |
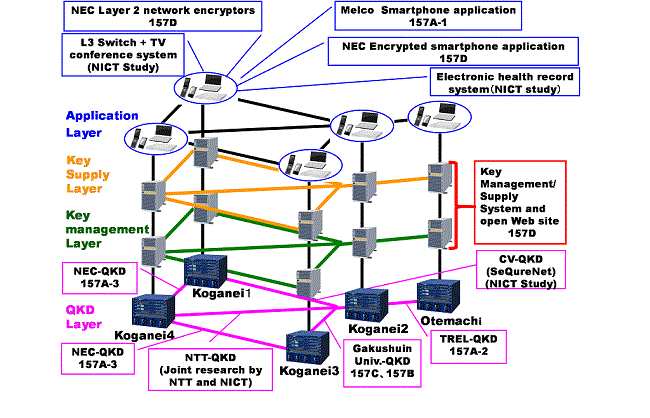
We integrated the research results of Subject 157A and 157C which were improved by suggestion from Subject 157B, and constructed the proof environment which consists of 5 nodes (Tokyo QKD Network). | Mar. 2016 | |
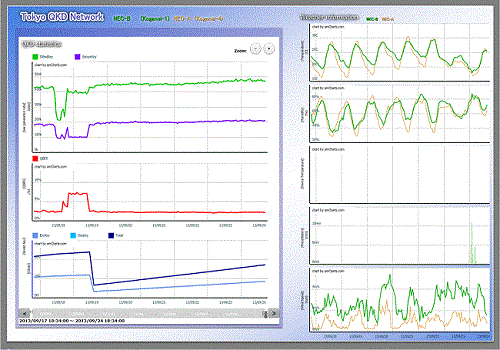
| We constructed a sensor network system to monitor environmental climate, where temperature and other climate data are displayed. We examined the effects of the climate on the performances of the QKD systems. | Mar. 2016 | ||
| When detecting a fiber tapping or an obstacle, the most suitable route of a key relay was selected and the route was switched automatically. We added the function to find the location of the tapping or the obstacle. | Mar. 2016 |
- We have defined a three layered structure for quantum key distribution.
- QKD systems are operated in the lowest layer to provide secure key to Key Management Agents (KMA) in the key management layer.
- The interface between the QKD layer and the key management layer is defined by key management agent library.
- The KMAs send key to Key Supply Agents (KSA) in the key supply layer.
- The KSAs supply key to applications, where API and file format are defined.
- Interface between QKD and KMA, and interface between KSA and application are fixed, so that any QKD systems and applications can participate the secure network as long as they obey the interface specification.
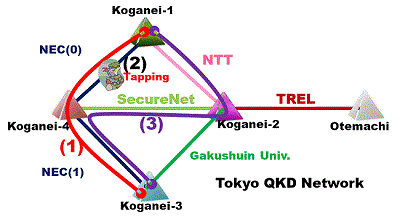
- (1) QKD-key is generated at (Red line) between Koganei-1 – Koganei-3 via Koganei-4.
- (2) Tapping occurs between Koganei-1 – Koganei-4.
- (3) A route is changed to (purple line) between Koganei-1 – Koganei-3 via Koganei-2 and Koganei-4.
Fig. 4Tokyo QKD Network
We have developed applications to prove the baseline model (Layer 2 network encryptors and Encrypted smartphone).
- We have developed practically useful quantum technology by exploiting classical techniques
- We proposed solution to the risk of trusted node quantum key relay
- We have also developed low-cost photon detectors for monitoring equipment
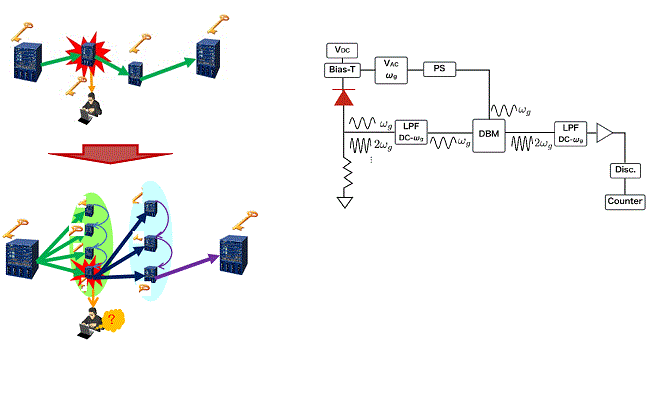
Fig. 6Quantum technology for secure network management
Risk of trusted node key relay
A simple receiver design with a balanced mixer
Only one compromised node leaks all information
Solution with group secter sharing
A photon detector works without sharp filter
Key is distributed many nodes, which can be regenerated by classical distributed computing.
Nodes can be compromised up to threshold number
Construction of test environment in collaboration with Subject 157A, 157B and 157C
Construction of test environment in collaboration with Subject 157A, 157B, and 157C
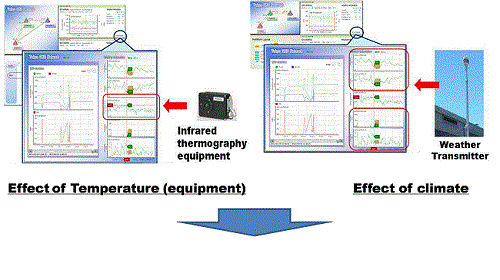 NEC's QKD equipment operates stably despite the change of temperature and climate
NEC's QKD equipment operates stably despite the change of temperature and climate
Fig. 8Temperature and climate effect
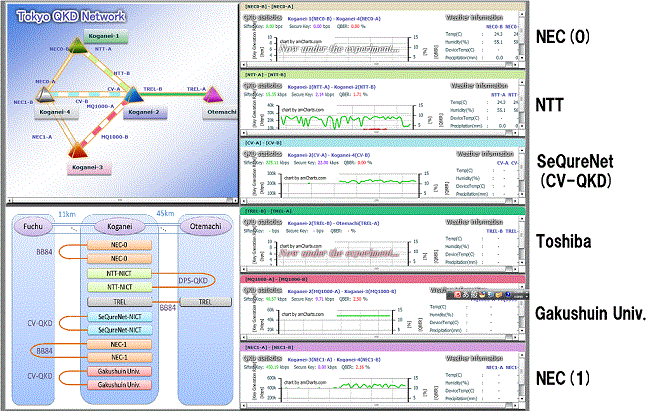
Fig. 9open Web site(1/2)  http://www.tokyoqkd.jp/
http://www.tokyoqkd.jp/
 We developed the secure network which combined modern cipher with quantum key distribution, and demonstrated secure communications on the Tokyo QKD Network in cooperation with Subject 157A and 157C.
We developed the secure network which combined modern cipher with quantum key distribution, and demonstrated secure communications on the Tokyo QKD Network in cooperation with Subject 157A and 157C.
 We will make effort to expand and diffuse the development of finding through ImPACT (FY2014-2018) project.
We will make effort to expand and diffuse the development of finding through ImPACT (FY2014-2018) project.