
Subject D : Secure photonic network architecture
157D-T01Architecture to install QKD systems into existing mission-critical-secure networks
NEC Corporation (Hironori Takahashi)
Hokkaido University
A higher priority in applications of our high-speed QKD systems is the one for state secret communications. Secure keys for one-time pad are conventionally delivered by trusted couriers. This system can be replaced with an automatic key delivery by a QKD network. Another important one is an application to secure data-backup communications. After the Great East Japan Earthquake, the importance of business continuity planning and constructing data backup networks for it has been widely recognized. QKD should be used to tightly protect transmission of confidential data between data centers and to make a mission-critical-secure communications system for the above purposes. We also develop an architecture of secure photonic network to provide multiuser secure services for medical networks, smart community networks, and so on.
We develop Secure Photonic Network architecture by the following four subthemes:
- Subtheme 1: Base-line model
- We derive baseline models for point-to-point link and point-to-multipoint network, which define the elements and specifications of the network, taking into account target applications. Fig. 1 depicts a rough image of a baseline model.
- Subtheme 2: Application of related peripheral technologies for management
- Secure Photonic Network must provide functions, such as authentication, key distribution and synchronization between several nodes, management of valid key. We develop an architecture for QKD network by integrating and customizing various technologies developed in modern cryptographic networks. The result will be integrated with quantum technology developed in Subtheme 3.
- Subtheme 3: Quantum cryptography technology for secure network management
- We explore quantum cryptographic technology to be useful for constructing secure network. Collaboration must be done with teams 157A, 157B, 157C respectively to modify the QKD system suitable to be adopted in the network. Finally, the results of subtheme 2 are integrated to the network as optimized architecture in terms of security and network resource.
- Subtheme 4: Construction of test environment and verification of operation
- After evaluation on the technologies developed from subthemes 2 and 3 in practice, a test environment according to the base-line model defined in subtheme 1 is developed. Then we study methods to combine the QKD technologies from teams 157A, 157B, 157C. Finally, a test service network is constructed according to the specification of the systems developed by these teams. The network includes a sensor system to monitor environmental conditions of optical fibers, interfaces, and status of the key management server and agents. It is widely expected that convincing data for quality guarantee of our secure photonic network will be beneficially extracted through test runs of the network.
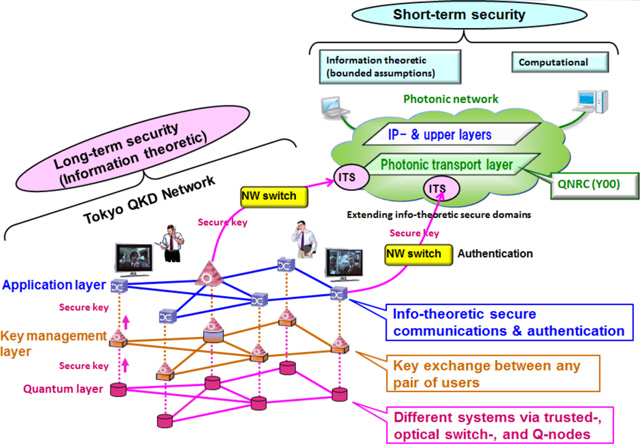
Fig. 1Concept
Interim results for Team 157D-T01
| Task title | Outcome | Date | Note |
|---|---|---|---|
| 1: Research for baseline model | We updated our original layer architecture (Fig. 1) to the four layer one by newly introducing the key supply (KS) layer. In the KS layer, as KS agent rearranges the key format so as to be used in various applications, authenticates devices in the application layer, and makes an interface between those devices and the KM agent. | Oct. 2013 | Demonstrated in Oct. 2013 |
| 2: Research for application of peripheral technologies | Validity of anonymous authentication was shown to achieve end-to-end communication security. Also versatile interface to the application layer was developed successfully. | Oct. 2013 | |
| 3: Research for application of quantum cryptography technology | A key relay protocol to reduce the risk on trusted nodes using quantum secret sharing within a group was proposed. The protocol shows improvement upon advantage either efficiency or safety to other protocols due to the combination of QKD, secret sharing, and distributed computing. (Fig. 4) |
Oct. 2013 | |
| 4: Network construction of environment and verification of operations | A test environment among individual sites has been provided which integrates different QKD systems developed by teams 157A and 157C. (Fig. 5) A sensor monitoring system was constructed to display temperature and other climate data with the QKD performance. (Figs. 6, 7-1, 7-2) |
Oct. 2013 |
We have defined a three layered structure for quantum key distribution, as follows (Figs. 2, 3):
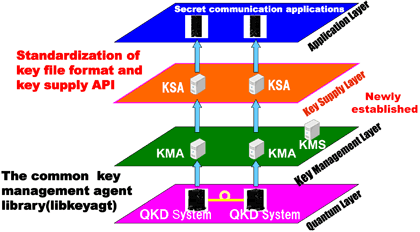
Fig. 2Three layer structure for quantum key distribution
- QKD systems are operated in the lowest layer to provide a secure key to Key Management Agents (KMA) in the key management layer.
- The interface between the quantum layer and the key management layer is defined by key management agent library.
- The KMAs send the key to Key Supply Agents (KSA) in the key supply layer.
- The KSAs supply the key to applications, where API and file format are defined.
- Interface between QKD and KMA, and interface between KSA and application, are fixed, so that any QKD systems and applications can participate the secure network on accordance with interface specification.
We have developed a key supply method in collaborated with teams 157A (NEC and MELCO). The structure was designed to have device independent interfaces (Fig. 3).
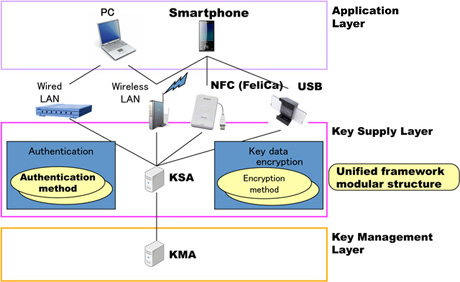
Fig. 3Structure of key supply method
With help of secret sharing idea, eavesdropper now must compromise all the node in one group and observe all the transmission on the parities P1,…Pn-1.
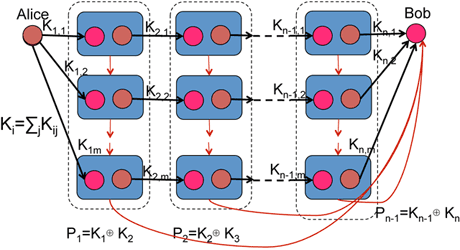
Fig. 4Reduction of the risk on the trusted nodes in key relay
Fig. 5 shows whole view of the construction of test environment in collaboration with teams 157A,157B,and 157C, named "Tokyo QKD Network 2013".
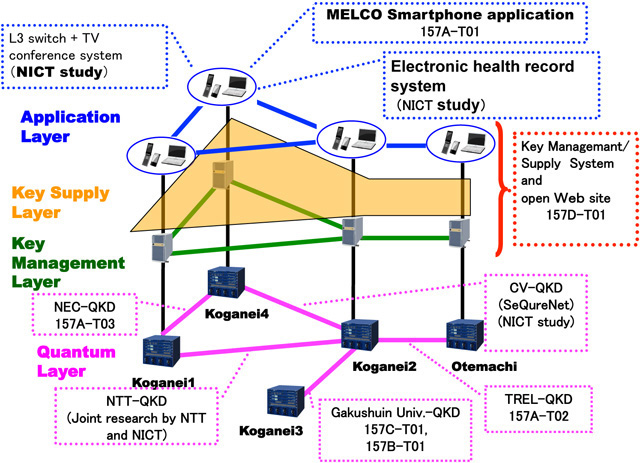
Fig. 5Tokyo QKD Network 2013
The sensor data monitoring system across the network displays actual time change up on Web page where temperature and other climate affect variance of the QKD machine performance. Below figure (Fig. 6) shows an example which has been done by collaboration with team 157A-T03 (NEC). The Web page developed as to be an actual monitor for different QKD system status data consolidated (Fig. 7).
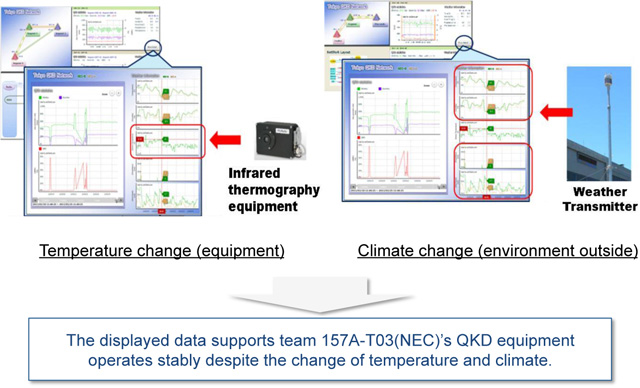
Fig. 6Monitor view on environmental dependence of the system
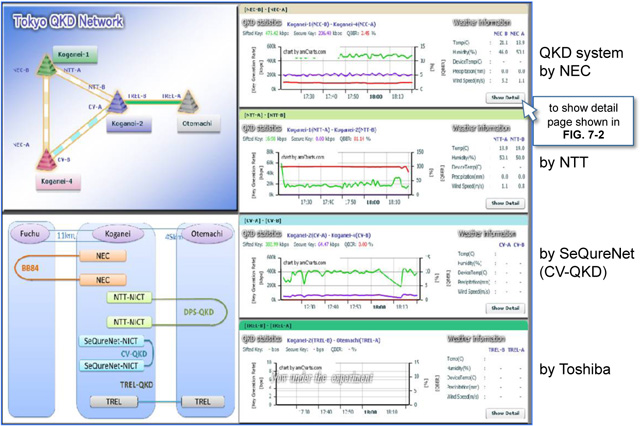
Fig. 7-1Open Web site page view (consolidated top)
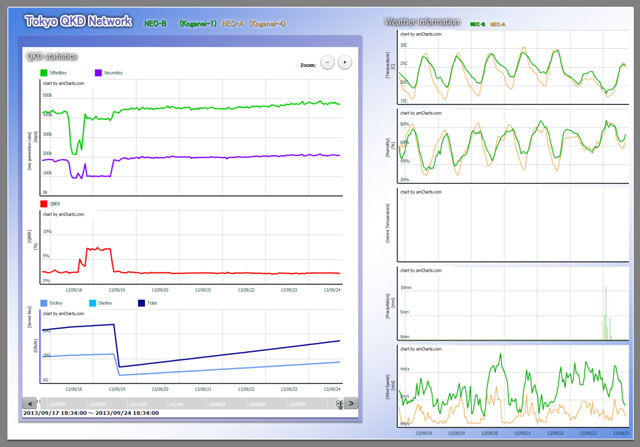
Fig. 7-2Open Web site page view (in detail for QKD system by NEC)
This page displays QKD performance; key rate (sift, secure), QBER, and saved key amount, and temperature/climate (in collaboration with team 157A-T02).
Targets for Team 157D-T01
| Task title | Work/Milestone | Due Date | Note |
|---|---|---|---|
| 4a: Construction of QKD platform (key management layer, key supply layer and application layer) | Construction of a secure photonic network by integrating QKD systems developed by teams 157A, 157C, and joint research projects. | Jan. 2015 | |
| 4b: Service of Secure photonic network | To start secure photonic network service | Jan. 2015 | |
| To complete long-term operation test of secure photonic network service | Dec. 2015 |
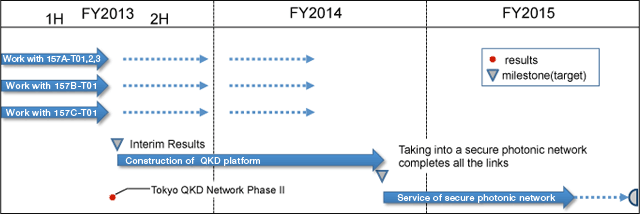
Chart 1Schedule for Team 157D-T01