Subject B : Quantum cryptographic theory
157B-T01Security certification and efficient key distillation
Nippon Telegraph and Telephone Corporation(NTT; Kiyoshi Tamaki)
Mitsubishi Electric Corporation
Hokkaido University
Nagoya University
Tokyo Institute of Technology(Titech)
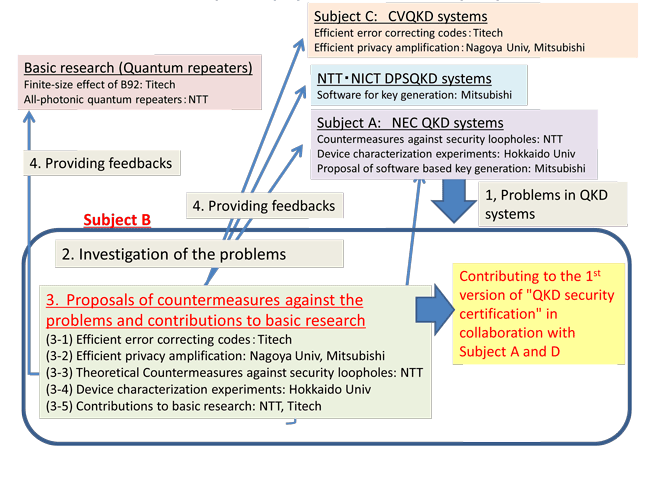
- Research loop in the project and contribution of Subject B
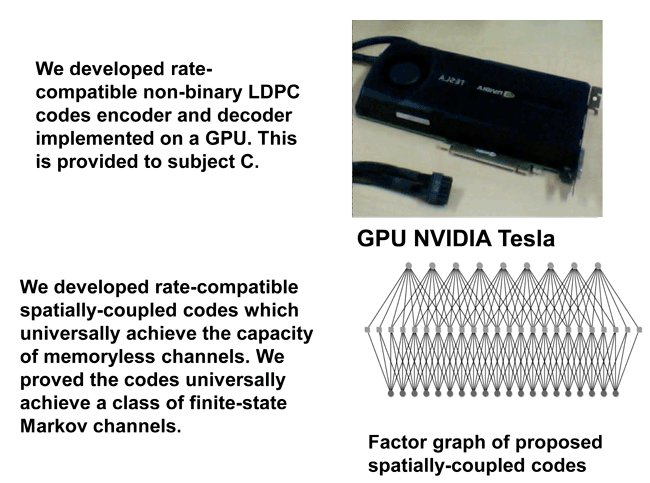
- (3-1) Efficient error correcting codes / Titech
- (3-2) Efficient Privacy amplification / Nagoya Univ., Mitsubishi
- (3-3) Theoretical Countermeasures against security loopholes / NTT
 Our protocol is now implemented by a number of experiments
Our protocol is now implemented by a number of experiments Our results are a step forward toward guaranteeing the implementation security of QKD
Our results are a step forward toward guaranteeing the implementation security of QKD- (3-4) Device characterization experiments / Hokkaido Univ.
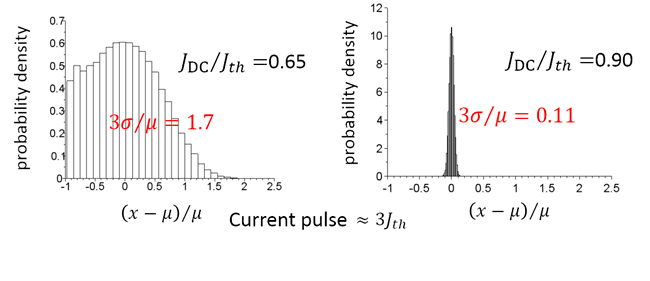
 Target range: 3σ / μ < 5%, determined from security theories
Target range: 3σ / μ < 5%, determined from security theories Intensity fluctuation was measured for a gain-switched LD
Intensity fluctuation was measured for a gain-switched LD Gain switching LD can satisfy the above criterion by strong excitation
Gain switching LD can satisfy the above criterion by strong excitation DC bias is limited by the phase correlation between pulses
DC bias is limited by the phase correlation between pulses Pulse current is limited by a LD-driver
Pulse current is limited by a LD-driver Large fluctuation was observed for weak excitation
Large fluctuation was observed for weak excitation We found unstable gain switching when the pulse period is comparable with carrier lifetime
We found unstable gain switching when the pulse period is comparable with carrier lifetime- (3-5) Contributions to basic research
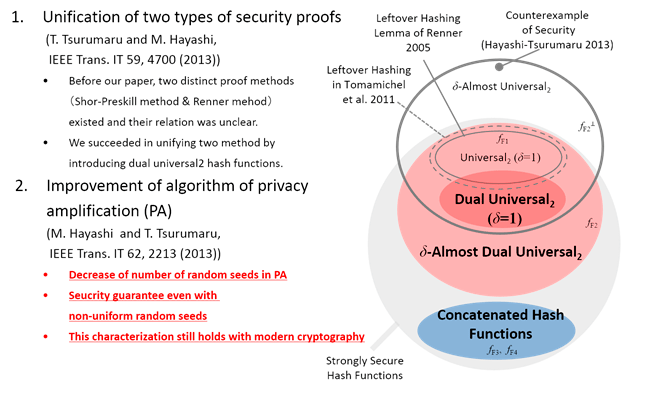
Proposal of dual unversal2 hash functionsa
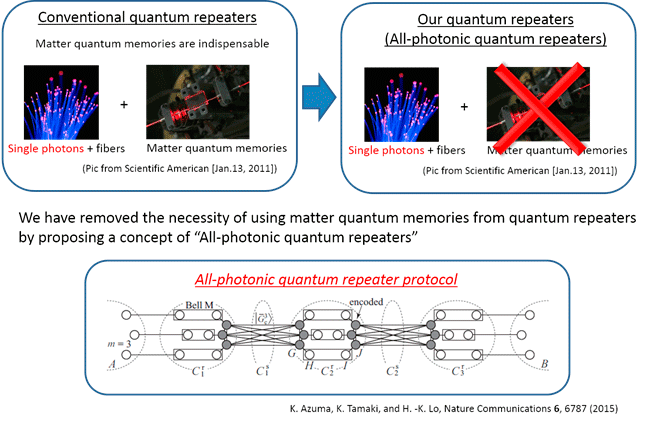
— From Quantum Cryptography to Modern Cryptography —
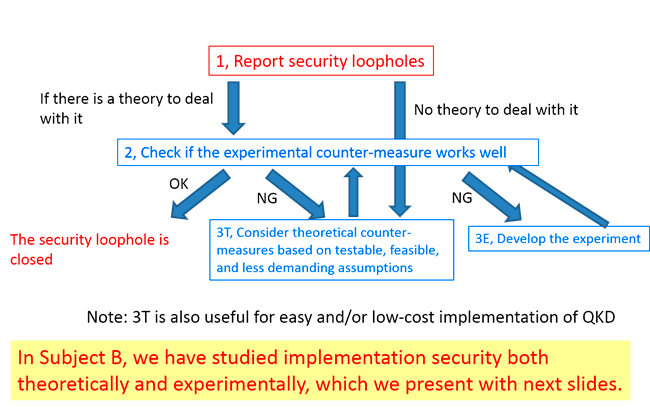
Research loop to close security loopholes
— Toward guaranteeing the implementation security —
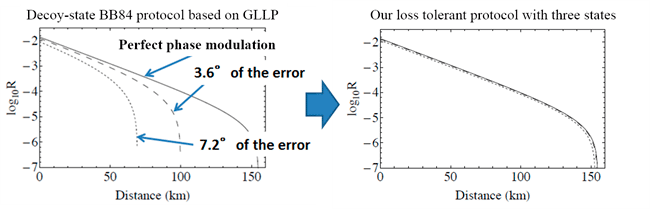
According to the existing analysis, called GLLP, the key rate R decreases significantly with slight imperfections in preparing the states. We have proposed "loss-tolerant protocol" to solve this problem, in which we exploit basis mismatched instances and only three flawed states.
K. Tamaki, M. Curty, G. Kato, H.-K. Lo, and K. Azuma, Phys. Rev. A 90, 052314 (2014).
Slide 5
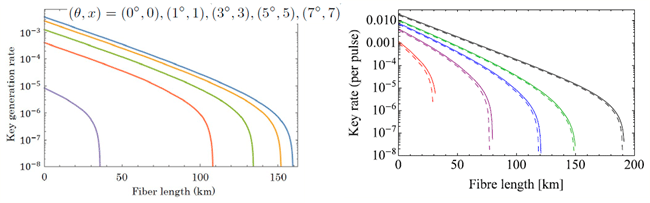
We have generalized our loss-tolerant protocol for easier characterization of the source and for taking into account the finite-size effect of the sending pulses.
| Easier characterization based on modulation regimes | Finite-size effect |
|---|
Slide 6
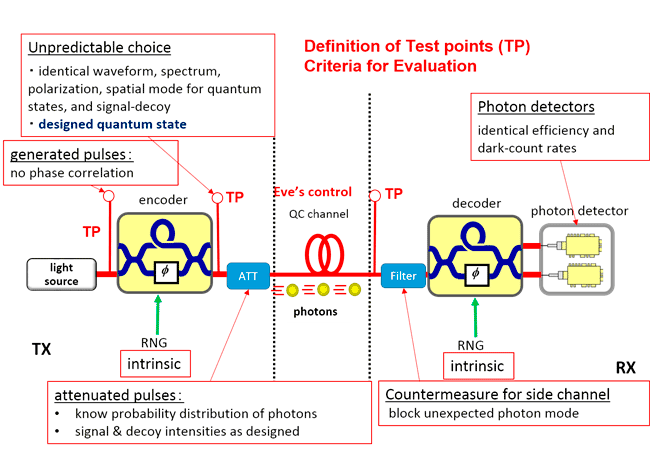
Requirements on device characteristics
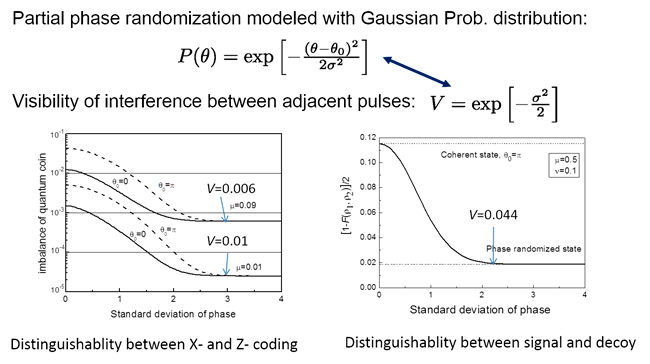
Criteria for phase randamization
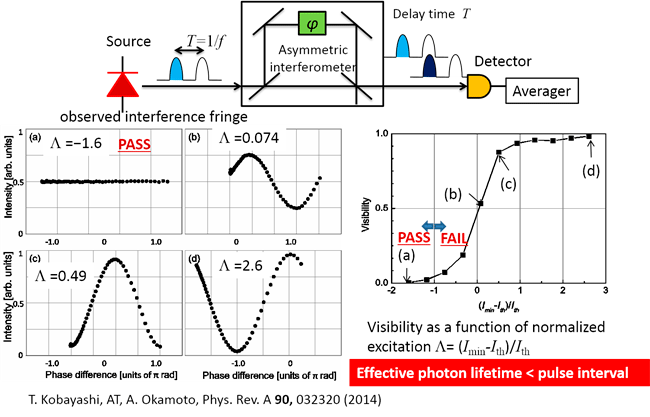
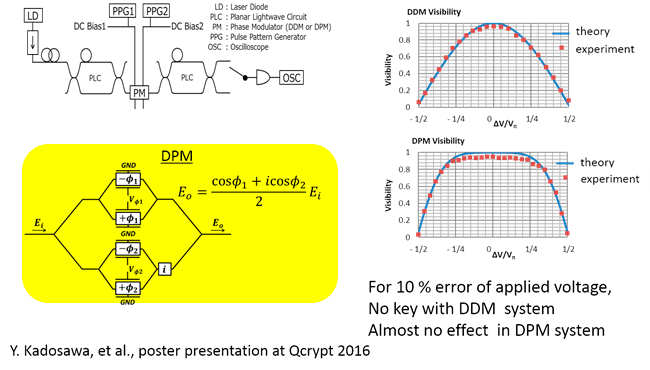
We related randomization to a mearsurable quantity: visibility of interface
Inter-pulse phase correlation for 10GHz
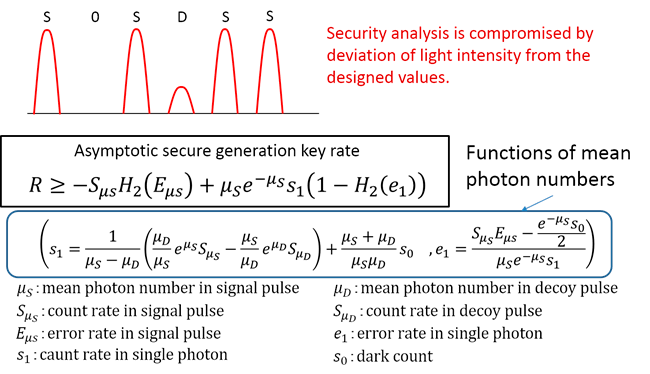
Intensity fluctuation in Decoy-state QKD
Intensity fluctuation in Gain-Switched LD
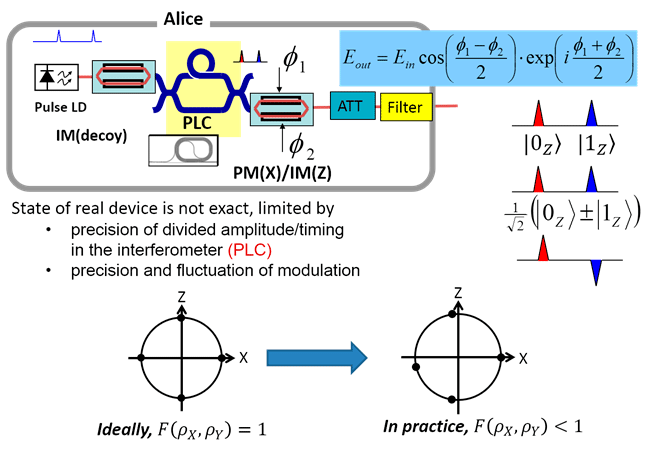
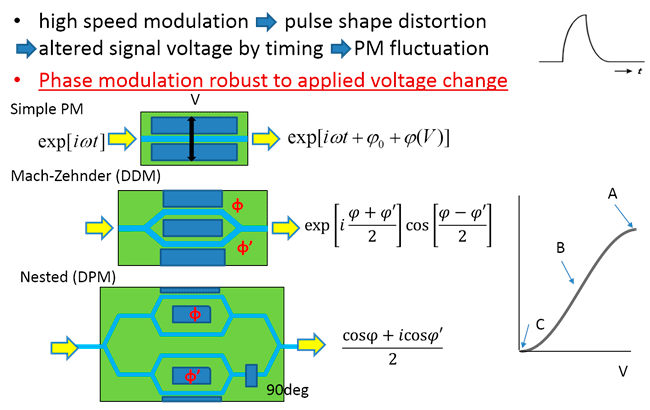
State preparation flaw
Improved implementation
Supression of phase uncertainty
Titech
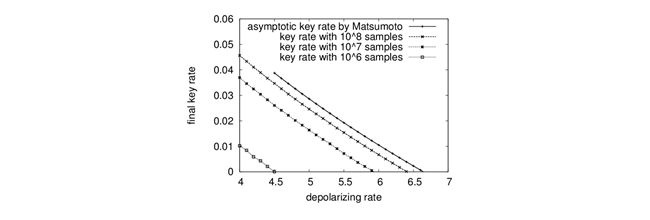
Before 2014, finite key length analysis of the B92 protocol had not been done. We applied the convex optimization technique previously introduced by us into the QKD area, and we obtained secure key rate of the B92 as above. (ISIT 2014).
NTT