
Subject B : Quantum cryptographic theory
157B-T01Security certification and efficient key distillation
Nippon Telegraph and Telephone Corporation (Kiyoshi Tamaki)
Mitsubishi Electric Corporation
Hokkaido University
Nagoya University
Tokyo Institute of Technology
It is well known that the security of QKD is guaranteed under the assumptions of the mathematical models of users’ devices. However, it is also well recognized that there exists a gap between the mathematical assumptions and the actual operations of the devices in the real world. Another issue of the current theory is the security evaluation with finite data size. In most of the security proofs, the security is guaranteed only assuming infinitely large data length whereas in the real QKD system the data size is obviously finite. The mission of our team is to fill this gap basically from a theoretical side. Our project consists of the following subthemes:
- Subtheme 1: Security analysis for finite size data
- In this subtheme, we will develop the post-processing technique to guarantee the security of key distribution schemes with finite data size.
- Subtheme 2: Development on efficient post-processing, privacy amplification, and error correction
- In this subtheme, we will develop more efficient and calculation cost effective algorithms for privacy amplification (PA), error correction (EC) and other post-processing operations.
- Subtheme 3: Device characterization and the security patch against side-channel attacks
- The gap between the mathematical model and real devices could be a room for eavesdroppers to efficiently attack the system. Such kind of attack is called “side-channel attacks” and should be seriously considered in practical QKD systems. In this subtheme, first we carefully analyze the given devices both theoretically and experimentally aiming to confirm the correctness of the device model and to strengthen privacy amplification to make the scheme secure. Also we develop new device configurations or even new QKD protocols that are free from or robust against side-channels.
- Subtheme 4: Security proofs for various protocols
- One reason that the main protocol pursued in the Secure Photonic Network Project is based on BB84 is because it is the most advanced protocol in the sense that its security proof including realistic conditions is relatively well developed. However, it does not necessarily mean that the other protocols are not useful in practice. In this subtheme, we will develop the theory of security analyses on various proposed protocols such as B92, DPS QKD and CV QKD.
Interim results for Team 157B-T01
| Task title | Outcome | Date | Note |
|---|---|---|---|
| 1: Security analysis for finite-size data | a) New theory for the finite-length security analysis of BB84 with a single photon source allowing the improvement of the key generation rate.Fig. 1a | Sep. 2012 | New J. Phys. 14, 093014 (2012) |
| b) New theory for the finite-length security analysis of the decoy methodFig. 1b | Jun. 2013 | QIP2013, TQC2012. | |
| 2: Development on efficient post-processing, PA, and ECFig. 2a | a) New class of hash functions formulated | Sep. 2012 | IEEE Trans. Info. Theory, 59, 4700 (2013) |
| b) Fast encoding algorithm for spatially-coupled LDPC codes developed | Jul. 2013 | IEEE ITW2012 (Invited poster) | |
| c) Implementation of the fast parallel error-correction decoding algorithm on GPGPU | Jul. 2013 | Installed on the CV QKD system developed in team 157C-T01 | |
| d) Fast and exact numerical computation algorithm for interval estimation of phase error rate (the single-photon BB84 key rate improved) | Aug. 2013 | QCrypt2013 | |
| 3: Device characterization and the security patch against side-channel attacks | a) New detector side-channel attack free (measurement device independent: MDI) QKD protocol proposedFig. 3a | Mar. 2012 |
|
| b) Novel optical circuits against the side-channel attack on phase modulators proposedFig. 3b | May 2012 | Patent applied | |
| c) Phase correlation measurement for gain-switched laser pulses up to 1GHzFig. 3c | Mar. 2013 | QCrypt2013 | |
| d) Novel optical circuits compensating the detection efficiency mismatch proposed | Sep. 2013 | Patent applied | |
| 4: Security proofs for various protocols | a) New security analysis of B92 resulting improved asymptotic key rates | Jul. 2013 | IEEE ISIT2013 |
| b) Security proof of CV QKD against calibration attacks on local oscillators | Aug. 2013 | QCrypt2013 | |
| c) Proof of unconditional security of the DPS QKD with block-wise phase randomization | Aug. 2013 | QCrypt2013 |
Targets for Team 157B-T01
| Task title | Work/Milestone | Due Date | Note |
|---|---|---|---|
| 5: System monitoring | |||
| 6: Random number generator | Proof-of-principle experiment | Mar. 2014 | |
| Proto-type development | Mar. 2016 | ||
| 7: Efficient key distillation algorithm for CVQKD | Design and implementation an efficient key distillation software for a CVQKD system. (with Gakushuin Univ. and TITECH) | ||
| Offline demonstration | Oct. 2013 | ||
| 8: Document for security certificate | To write a document for security certificate of QKD | Mar. 2016 |
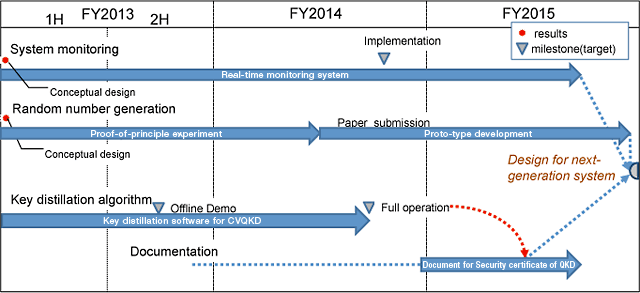
Chart 1Schedule for Team 157B-T01