The Tokyo QKD network is constructed in a part of the NICT open test-bed network "Japan Giga Bit Network 2 plus". It was inaugurated on 14th October 2010. A live demonstration of QKD network operations including absolutely secure video transmission, detection of an eavesdropper, and rerouting to the secondary secure link, was demonstrated to the public in the conference UQCC2010 (18-20 October) by the project teams consisting of NICT, NEC, Mitsubishi Electric, NTT, Toshiba Research Europe, ID Quantique, the Austrian Institute of Technology, the Institute of Quantum Optics and Quantum Information and the University of Vienna, demonstrated to the public QKD network operations on this test-bed. It shall function as a cooperation platform between Japanese and overseas research organizations to disseminate outcomes of quantum cryptography and communications for the benefit of society.
The Tokyo QKD network is now under the reconstruction in the new test-bed environment, "JGN-X" (JGN-eXtreme). It will start new research and development from September 2011, having renewed research teams under the NICT commissioned research in the third mid-term plan, called the Quantum Phase III (2011-2015).
Latest Results of Field Test
→Middle-term operation performance of QKD over 90 km
Papers Update
- Summary paper on the Tokyo QKD Network
- M. Sasaki, et al.,
"Field test of quantum key distribution in the Tokyo QKD Network,"
Opt. Express 19 (11), pp10387--10409 (2011)
- Potential security threat : Inter fiber cross-talk
- M. Fujiwara, S. Miki, T. Yamashita, Z. Wang, and M. Sasaki,
"Photon level crosstalk between parallel fibers installed in urban area,"
Opt. Express. 18 (21), pp 22199 --22207 (2010).
QKD Network Operation in October 2010
The live demonstration of QKD was performed in an international collaboration by NICT, NEC, Mitsubishi Electric, NTT, Toshiba Research Europe Ltd., ID Quantique, and All Vienna (the Austrian Institute of Technology, the Institute for Quantum Optics and Quantum Information and the University of Vienna).
The Tokyo QKD network is configured as a star network connecting the JGN2plus operation center in Otemachi with NICT's Headquarter in Koganei as well as Tokyo University in Hongo and NICT's research facility in Hakusan. (Fig. 1 below)
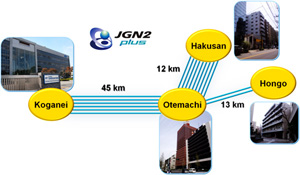
Fig. 2 summarizes physical installation of their QKD devices. There are totally 6 links. Some of them are in a loop back configuration.
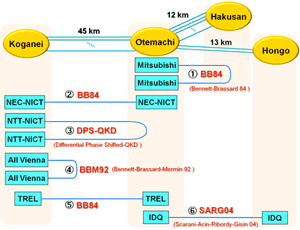
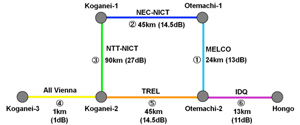
The Logical Structure can be viewed as a mesh network consisting of six nodes, as shown in Fig. 3. The fibers are really lossy. The loss rates are between 0.3 and 0.5 dB per km.
We adopted a three-layer architecture based on trusted nodes, as shown Fig. 4. The quantum layer consists of point-to-point quantum links, forming the QBB. Each link generates the secure key in its own way. The protocols and key format can be arbitrary. QKD devices push the key materials to the key management layer.
In this middle layer, a key management agent (KMA) locates at each site, and works as a trusted node. Each KMA receives the key material, and resizes and saves them as well as to store QBER and key generation rate. Key relay is performed by OTP-capsulation in a hop-by-hop fashion. In each agent, advanced encryption standard is also implemented, beside one-time pad. They can be switched, depending on residual amounts of secure keys.
In the communication layer, various applications such as secure TV conferencing and key downloading to mobile phones are performed. The video encryption rate is 128 kbps in a stored key mode.
Finally, a key management server (KMS) gathers link information from KMAs, organizes a routing table, and provisions secure paths to KMAs. Wegman-Carter authentication codes are implemented in KMS and KMAs.
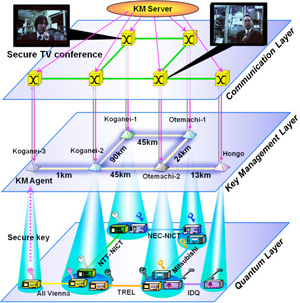
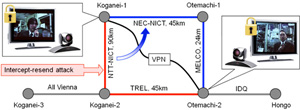
We demonstrated secure TV conference between Koganei and Otemachi. Secure key can be provided by two QKD relay routes, shown by red and blue lines as shown in Fig. 5. An eavesdropping device was set in the link in red. The KMAs monitor the bit error rate in every 5 sec. The bit error rate soon increased. The agents notice that the NTT link was hacked, and stop the key generation in this kink, raising an alarm in the KMS. The secure TV conference continues by using the remaining key, but it is running short. So the server gives instruction to switch to the secondary route. It consists of the NEC and Mitsubishi links. Thus the TV conference could continue unimpeded.
Figures 1-5 jpg files available below.
Fig. 1 / Fig. 2 / Fig. 3 / Fig. 4 / Fig. 5
Prospects
After sufficient tests of long-term operation stability in the Tokyo QKD Network, QKD systems are expected to be deployed first in the NICT internal networks. They will then be installed into government agencies networks and mission critical infrastructures where communication security is imperative to protect state secrets. Further improvements in device compactness will then expand the application area of QKD to financial, medical and business organizations for the well-being of the public.
[ Page Top ]

